Wireguard and Wireguard over VXLAN tunnel automation
In this guide we will explore how to set up the automatic management of Wireguard or Wireguard over VXLAN tunnels.
How to setup WireGuard tunnels
Follow the procedure described below to setup WireGuard tunnels on your devices.
Note: This example uses Shared systemwide (no organization) option as the organization for VPN server and VPN client template. You can use any organization as long as VPN server, VPN client template and Device has same organization.
1. Create VPN server configuration for WireGuard
Visit
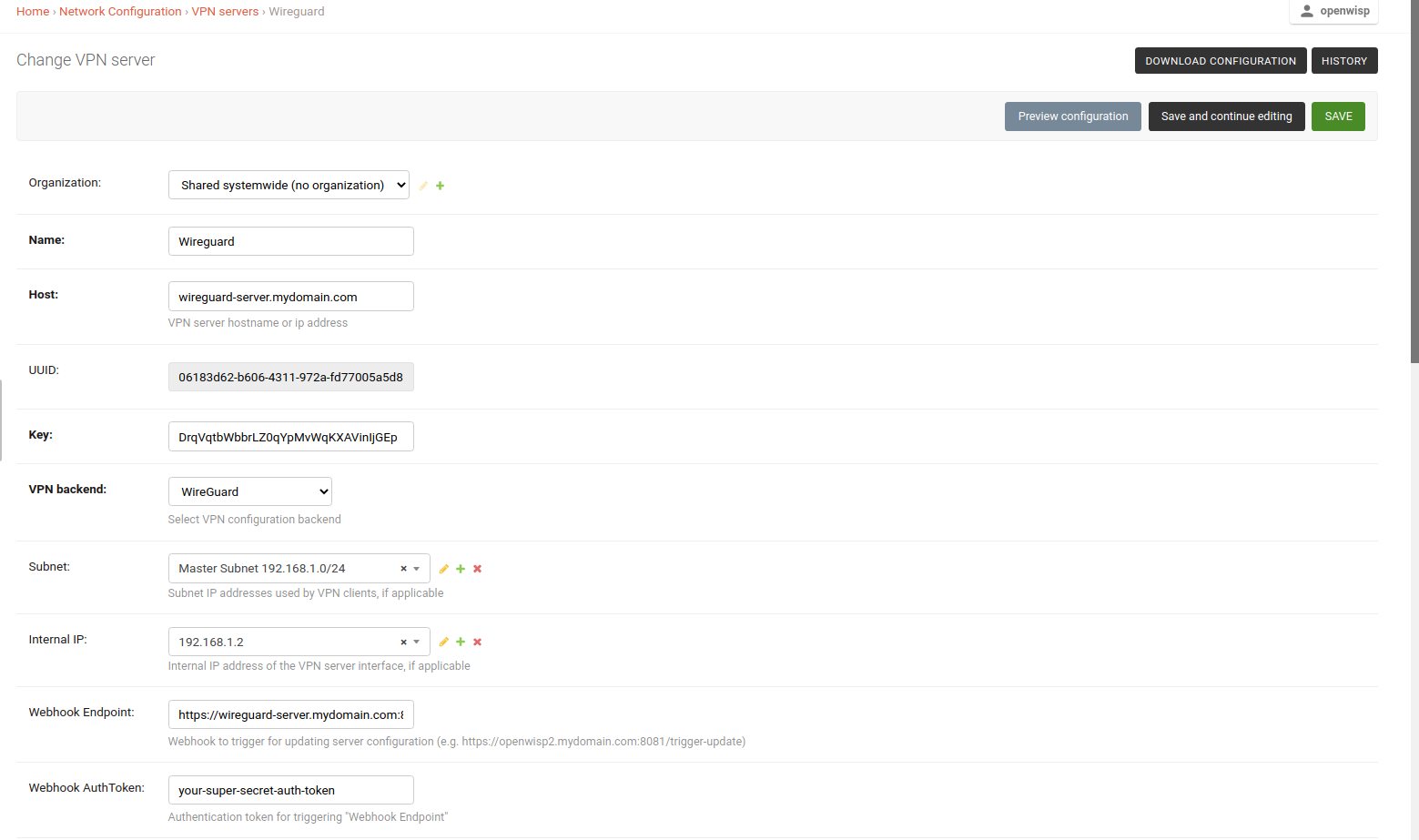
/admin/config/vpn/add/to add a new VPN server.We will set Name of this VPN server
Wireguardand Host aswireguard-server.mydomain.com(update this to point to your WireGuard VPN server).Select
WireGuardfrom the dropdown as VPN Backend.When using WireGuard, OpenWISP takes care of managing IP addresses (assigning an IP address to each VPN peer). You can create a new subnet or select an existing one from the dropdown menu. You can also assign an Internal IP to the WireGuard Server or leave it empty for OpenWISP to configure. This IP address will be used by the WireGuard interface on server.
We have set the Webhook Endpoint as
https://wireguard-server.mydomain.com:8081/trigger-updatefor this example. You will need to update this according to you VPN upgrader endpoint. Set Webhook AuthToken to any strong passphrase, this will be used to ensure that configuration upgrades are requested from trusted sources.Note
If you are following this tutorial for also setting up WireGuard VPN server, just substitute
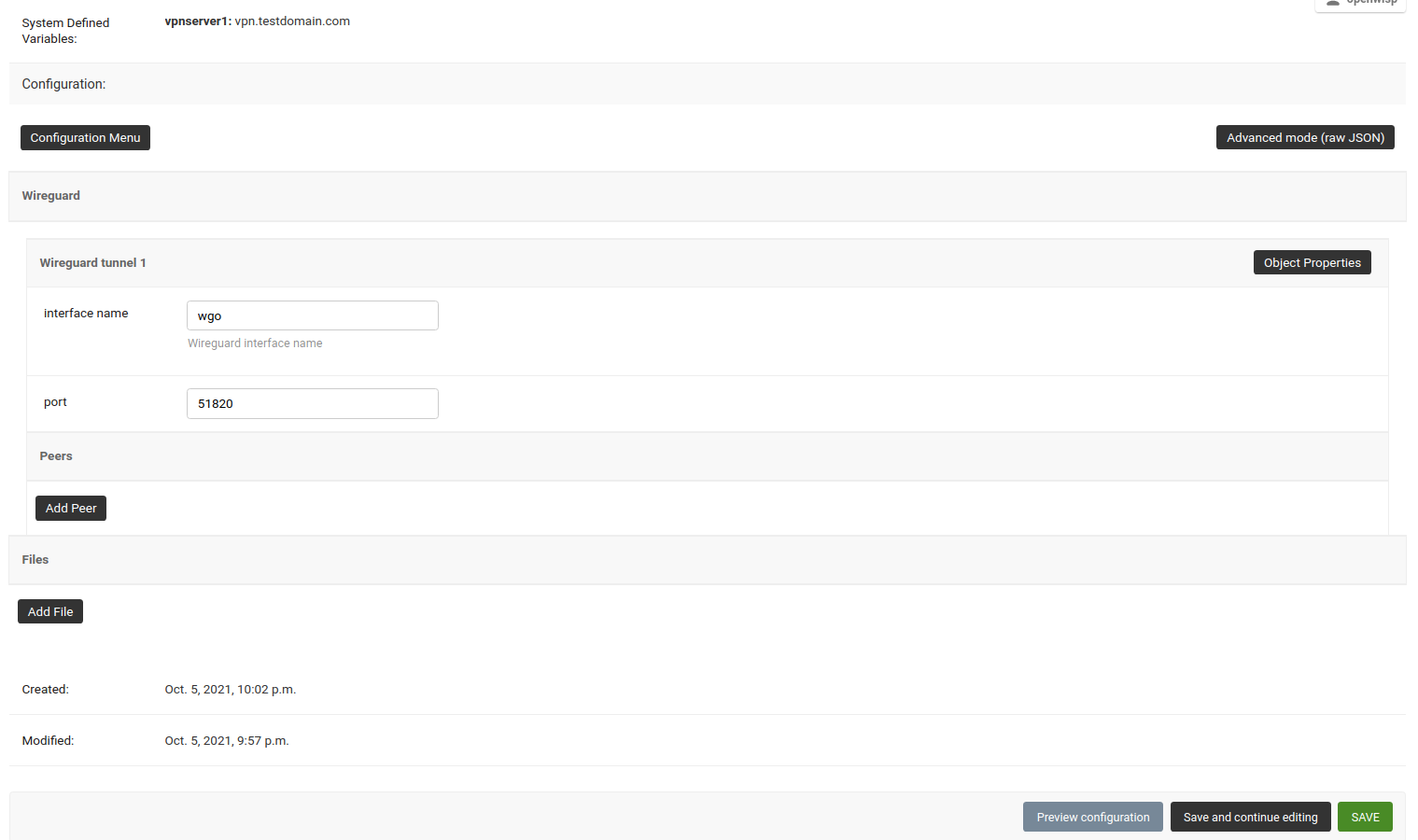
wireguard-server.mydomain.comwith hostname of your VPN server and follow the steps in next section.Under the configuration section, set the name of WireGuard tunnel 1 interface. We have used
wg0in this example.
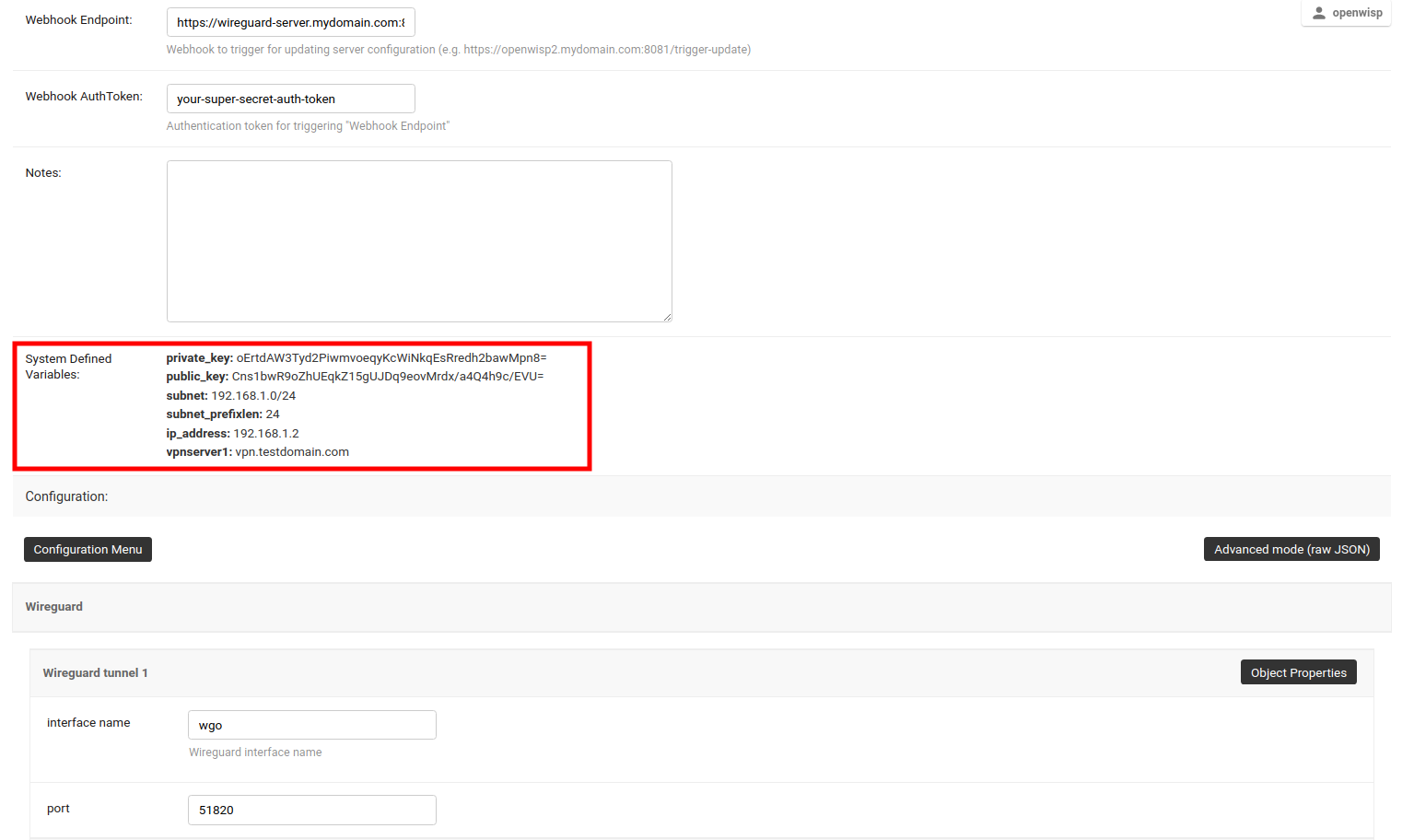
After clicking on Save and continue editing, you will see that OpenWISP has automatically created public and private key for WireGuard server in System Defined Variables along with internal IP address information.
2. Deploy Wireguard VPN Server
If you haven't already setup WireGuard on your VPN server, this will be a good time do so.
We recommend using the ansible-wireguard-openwisp role for installing WireGuard since it also installs scripts that allows OpenWISP to manage WireGuard VPN server.
Pay attention to the VPN server attributes used in your playbook. It should be same as VPN server configuration in OpenWISP.
3. Create VPN client template for WireGuard VPN Server
Visit
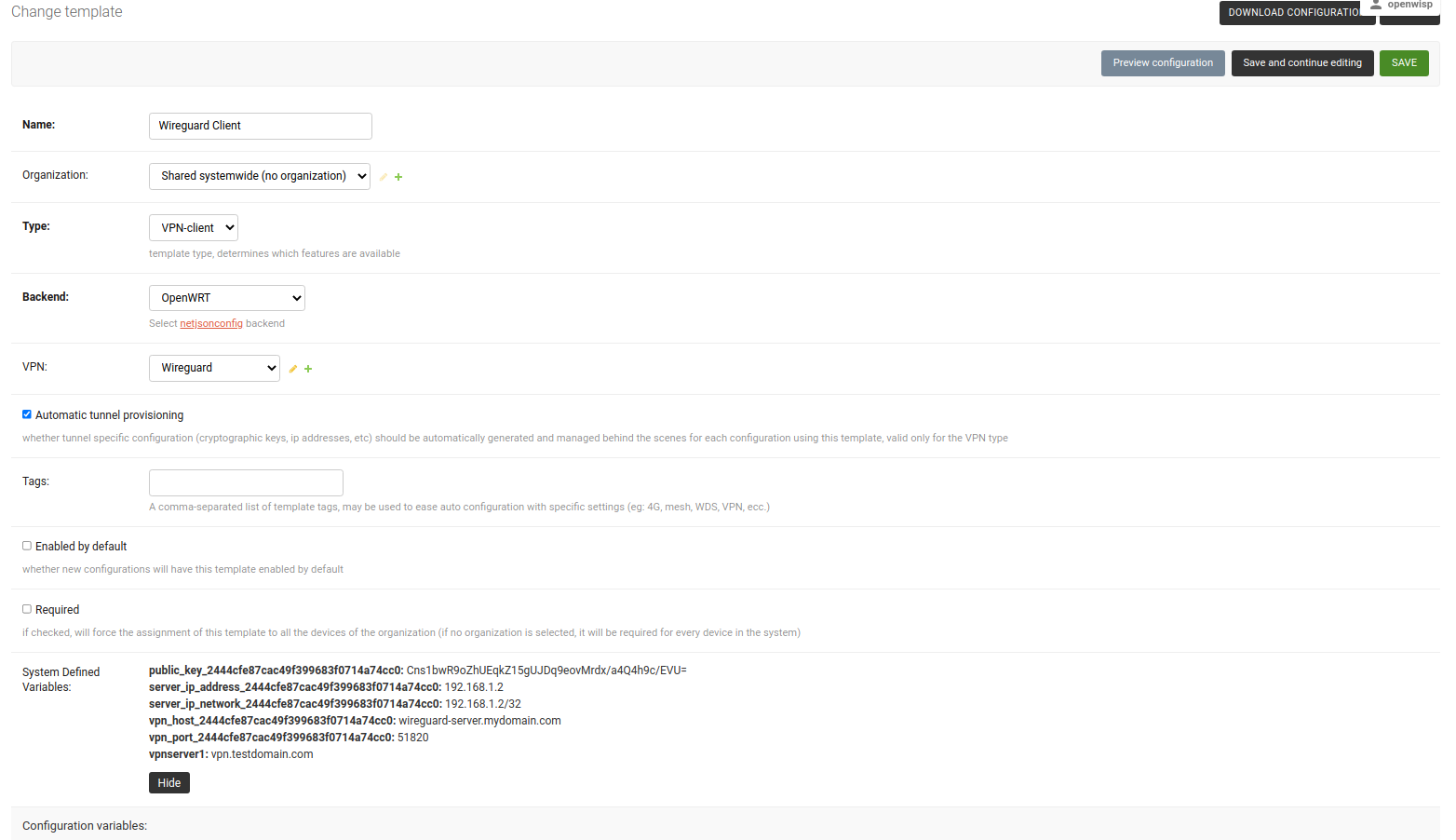
/admin/config/template/add/to add a new template.Set
Wireguard Clientas Name (you can set whatever you want) and selectVPN-clientas type from the dropdown list.The Backend field refers to the backend of the device this template can be applied to. For this example, we will leave it to
OpenWRT.Select the correct VPN server from the dropdown for the VPN field. Here it is
Wireguard.Ensure that Automatic tunnel provisioning is checked. This will make OpenWISP to automatically generate public and private keys and provision IP address for each WireGuard VPN client.
After clicking on Save and continue editing button, you will see details of Wireguard VPN server in System Defined Variables. The template configuration will be automatically generated which you can tweak accordingly. We will use the automatically generated VPN client configuration for this example.
4. Apply Wireguard VPN template to devices
Note
This step assumes that you already have a device registered on OpenWISP. Register or create a device before proceeding.
Open the Configuration tab of the concerned device.
Select the WireGuard Client template.
Upon clicking on Save and continue editing button, you will see some entries in System Defined Variables. It will contain internal IP address, private and public key for the WireGuard client on the device along with details of WireGuard VPN server.
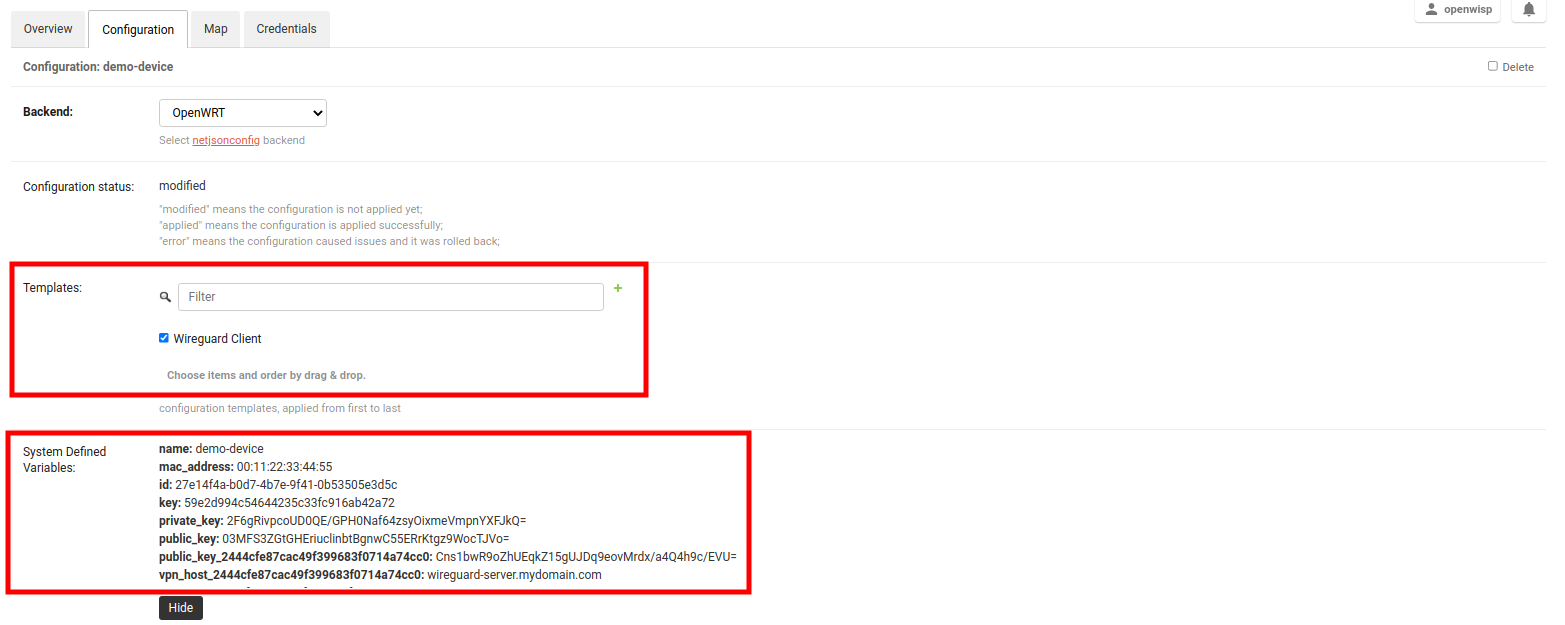
Voila! You have successfully configured OpenWISP to manage WireGuard tunnels for your devices.
How to setup VXLAN over WireGuard tunnels
By following these steps, you will be able to setup layer 2 VXLAN tunnels encapsulated in WireGuard tunnels which work on layer 3.
Note: This example uses Shared systemwide (no organization) option as the organization for VPN server and VPN client template. You can use any organization as long as VPN server, VPN client template and Device has same organization.
1. Create VPN server configuration for VXLAN over WireGuard
Visit
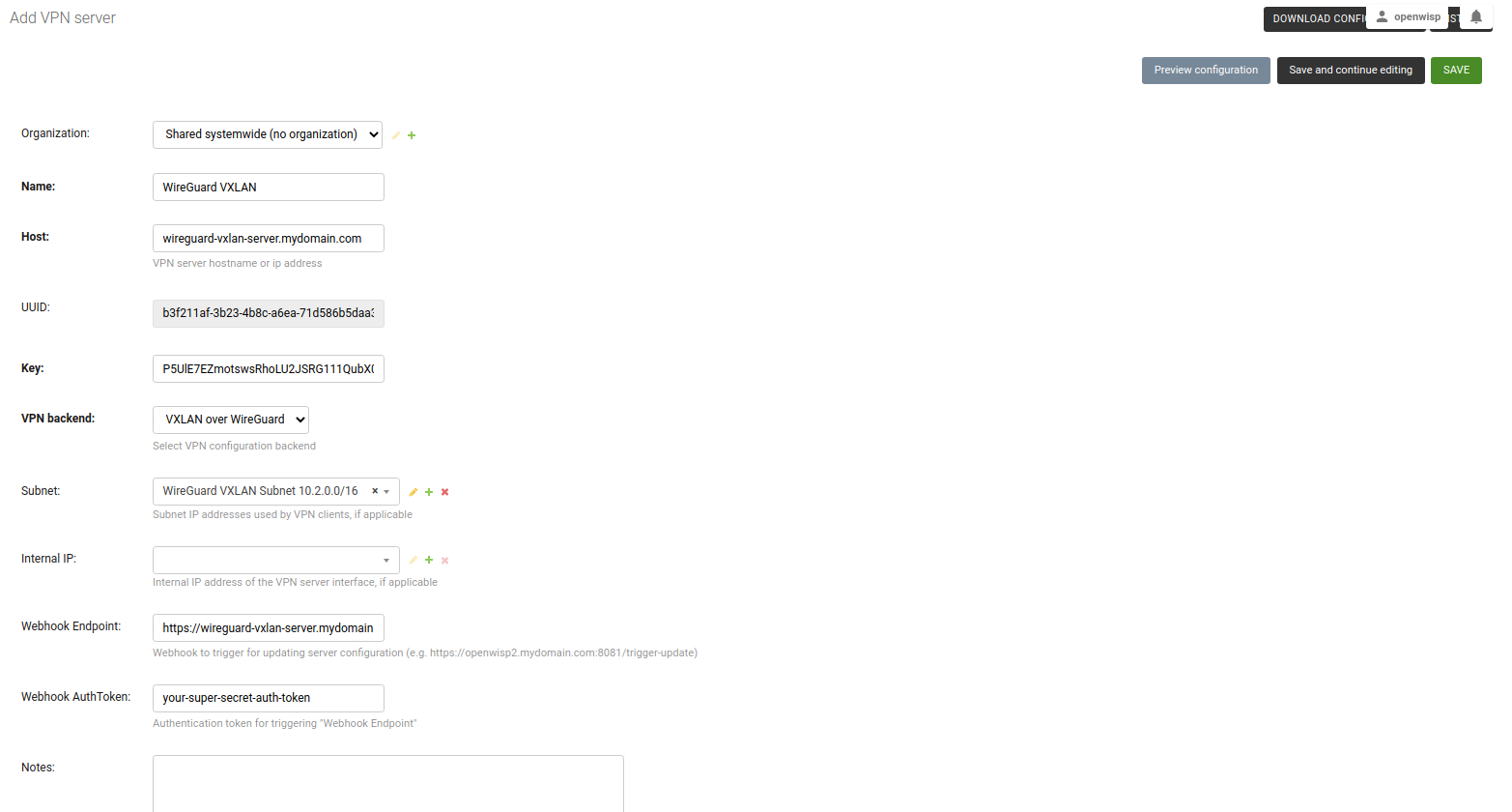
/admin/config/vpn/add/to add a new VPN server.We will set Name of this VPN server
Wireguard VXLANand Host aswireguard-vxlan-server.mydomain.com(update this to point to your WireGuard VXLAN VPN server).Select
VXLAN over WireGuardfrom the dropdown as VPN Backend.When using VXLAN over WireGuard, OpenWISP takes care of managing IP addresses (assigning an IP address to each VPN peer). You can create a new subnet or select an existing one from the dropdown menu. You can also assign an Internal IP to the WireGuard Server or leave it empty for OpenWISP to configure. This IP address will be used by the WireGuard interface on server.
We have set the Webhook Endpoint as
https://wireguard-vxlan-server.mydomain.com:8081/trigger-updatefor this example. You will need to update this according to you VPN upgrader endpoint. Set Webhook AuthToken to any strong passphrase, this will be used to ensure that configuration upgrades are requested from trusted sources.Note
If you are following this tutorial for also setting up WireGuard VPN server, just substitute
wireguard-server.mydomain.comwith hostname of your VPN server and follow the steps in next section.Under the configuration section, set the name of WireGuard tunnel 1 interface. We have used
wg0in this example.
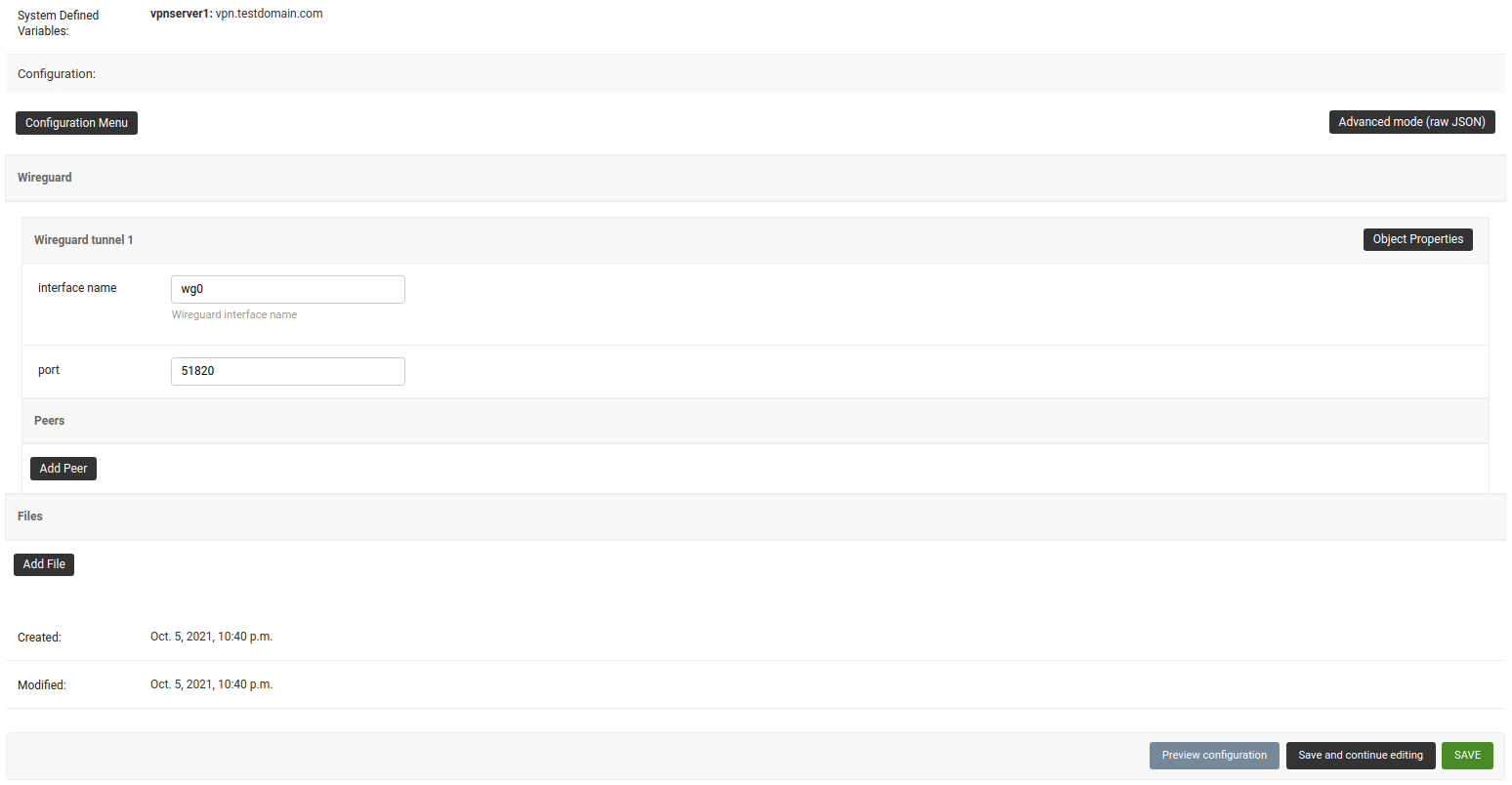
After clicking on Save and continue editing, you will see that OpenWISP has automatically created public and private key for WireGuard server in System Defined Variables along with internal IP address information.
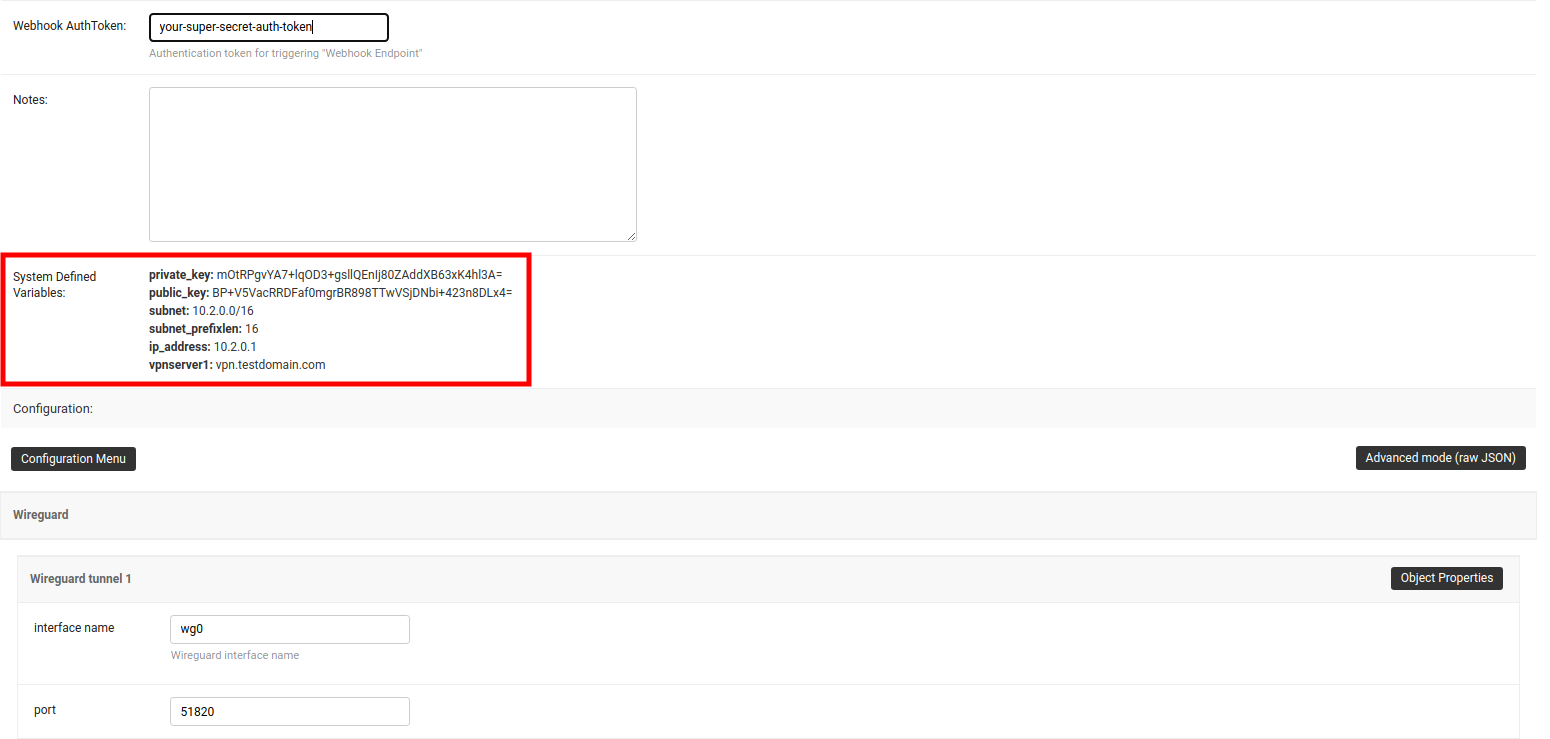
2. Deploy Wireguard VXLAN VPN Server
If you haven't already setup WireGuard on your VPN server, this will be a good time do so. We recommend using the ansible-wireguard-openwisp role for installing WireGuard since it also installs scripts that allows OpenWISP to manage WireGuard VPN server along with VXLAN tunnels.
Pay attention to the VPN server attributes used in your playbook. It should be same as VPN server configuration in OpenWISP.
3. Create VPN client template for WireGuard VXLAN VPN Server
Visit
/admin/config/template/add/to add a new template.Set
Wireguard VXLAN Clientas Name (you can set whatever you want) and selectVPN-clientas type from the dropdown list.The Backend field refers to the backend of the device this template can be applied to. For this example, we will leave it to
OpenWRT.Select the correct VPN server from the dropdown for the VPN field. Here it is
Wireguard VXLAN.Ensure that Automatic tunnel provisioning is checked. This will make OpenWISP to automatically generate public and private keys and provision IP address for each WireGuard VPN client along with VXLAN Network Identifier (VNI).
After clicking on Save and continue editing button, you will see details of Wireguard VXLAN VPN server in System Defined Variables. The template configuration will be automatically generated which you can tweak accordingly. We will use the automatically generated VPN client configuration for this example.
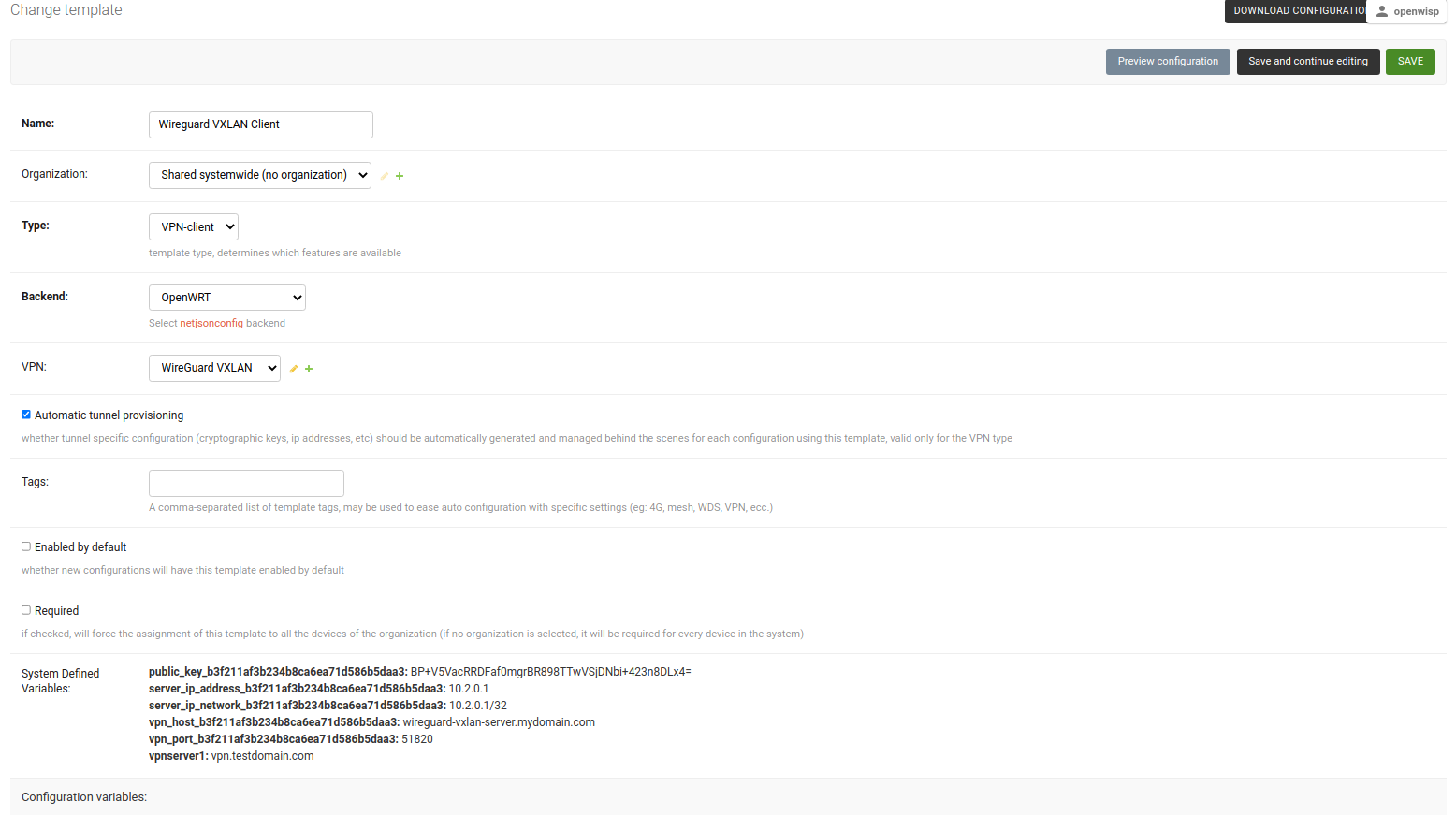
4. Apply Wireguard VXLAN VPN template to devices
Note
This step assumes that you already have a device registered on OpenWISP. Register or create a device before proceeding.
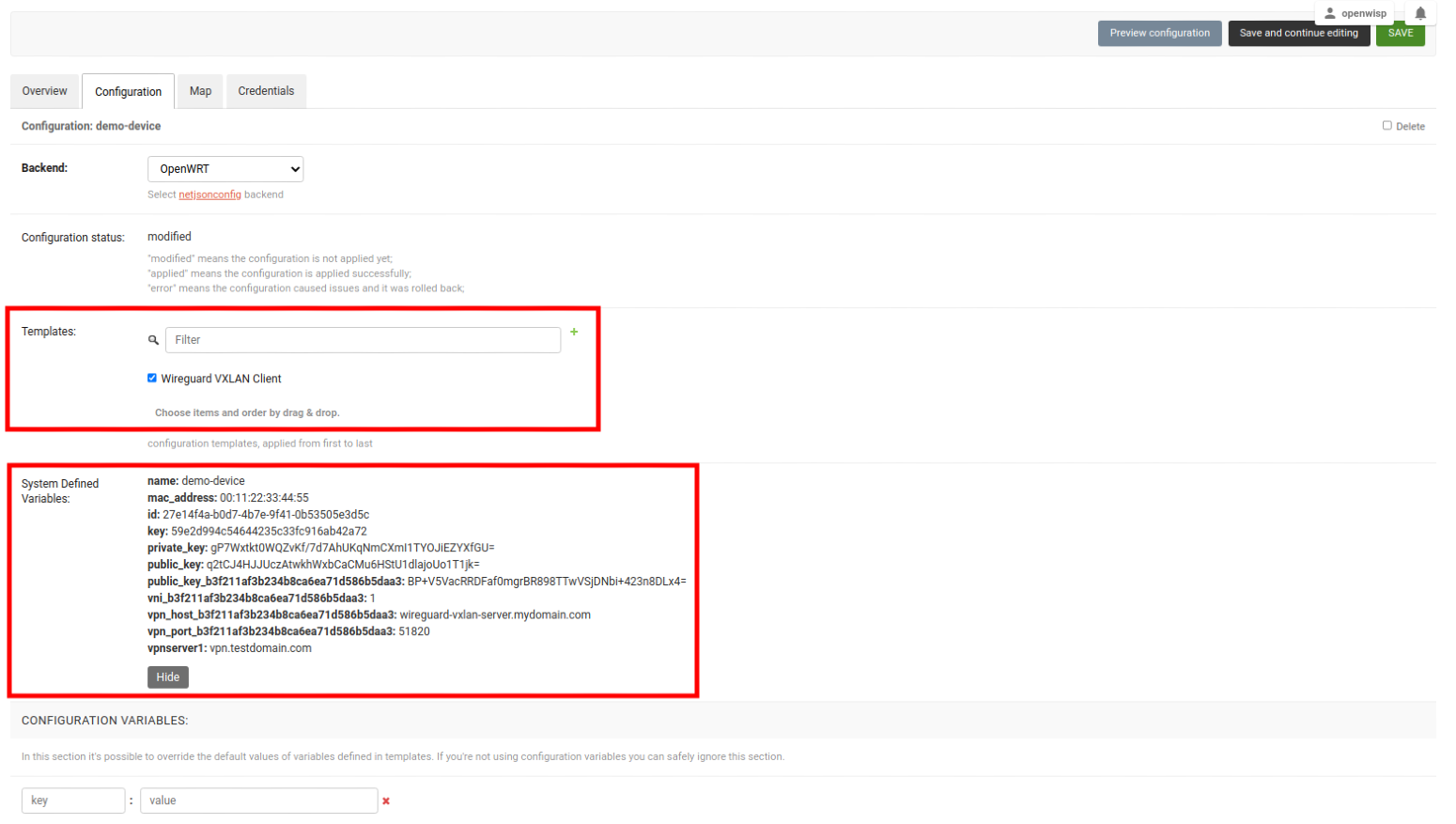
Open the Configuration tab of the concerned device.
Select the WireGuard VXLAN Client template.
Upon clicking on Save and continue editing button, you will see some entries in System Defined Variables. It will contain internal IP address, private and public key for the WireGuard client on the device and details of WireGuard VPN server along with VXLAN Network Identifier (VNI) of this device.
Voila! You have successfully configured OpenWISP to manage VXLAN over WireGuard tunnels for your devices.