Automating ZeroTier Tunnels
Important
This guide assumes your OpenWrt firmware has the zerotier package
installed. If this package is not present, you will need to install
it.
Follow the procedure described below to set up ZeroTier tunnels on your devices.
Note
This guide creates the VPN server and VPN client templates as Shared systemwide (no organization) objects. This allows any device of any organization to use the automation.
If needed, you can use any organization as long as the VPN server, the VPN client template, and devices have the same organization.
1. Configure Self-Hosted ZeroTier Network Controller
If you haven't already set up a self-hosted ZeroTier network controller on your server, now is a good time to do so. You can start by simply installing ZeroTier on your server from the official website.
2. Create VPN Server Configuration for ZeroTier
Visit
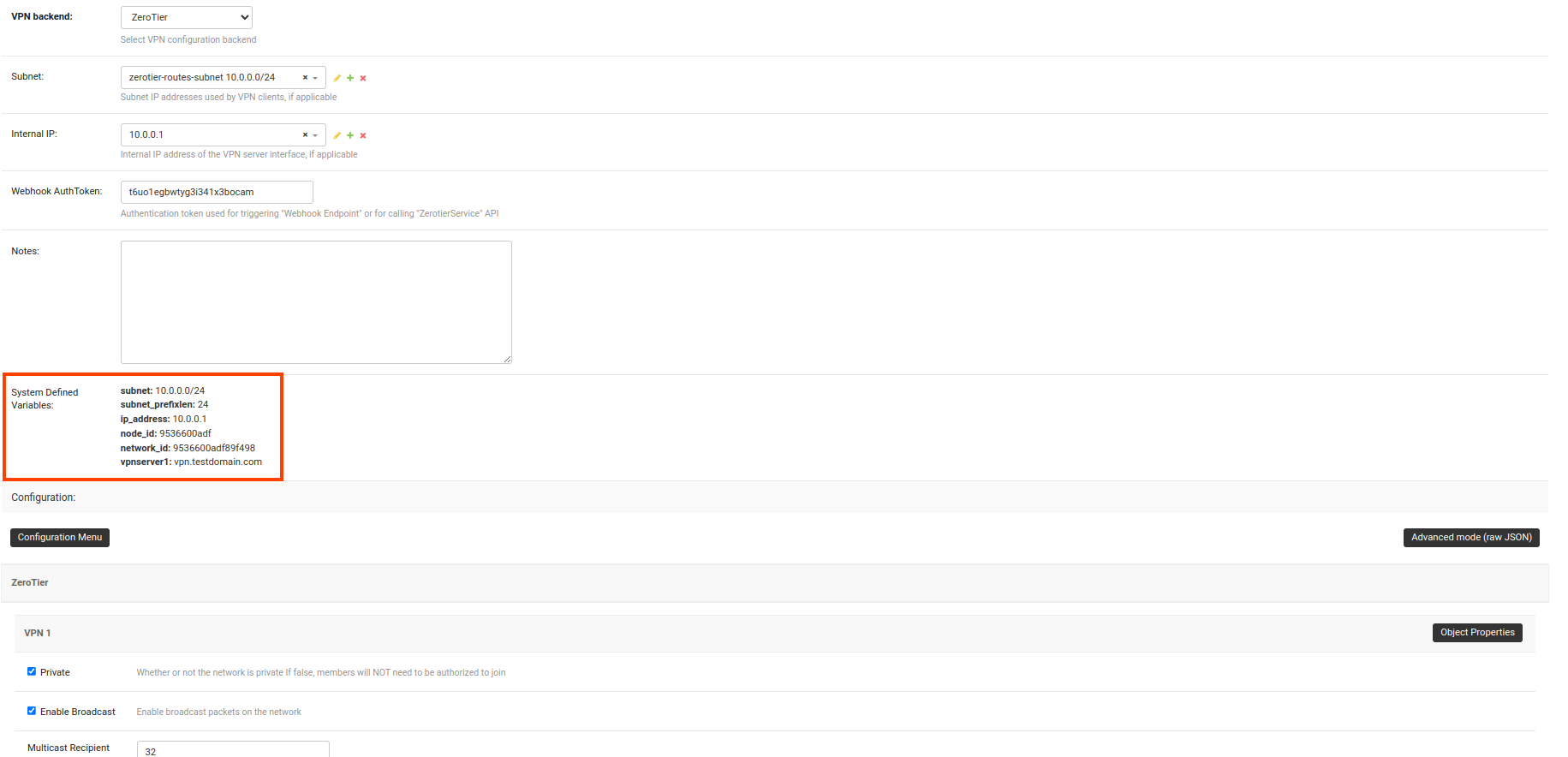
/admin/config/vpn/add/to add a new VPN server.We will set Name of this VPN server
ZeroTierand Host asmy-zerotier-server.mydomain.com:9993(update this to point to your ZeroTier VPN server).Select
ZeroTierfrom the dropdown as VPN Backend.When using ZeroTier, OpenWISP takes care of managing IP addresses (assigning an IP address to each VPN client (ZeroTier network members)). You can create a new subnet or select an existing one from the dropdown menu. You can also assign an Internal IP to the ZeroTier controller or leave it empty for OpenWISP to configure. This IP address will be used to assign it to the ZeroTier controller running on the server.
Set the Webhook AuthToken, this will be the ZeroTier authorization token which you can obtain by running the following command on the ZeroTier controller:
sudo cat /var/lib/zerotier-one/authtoken.secret
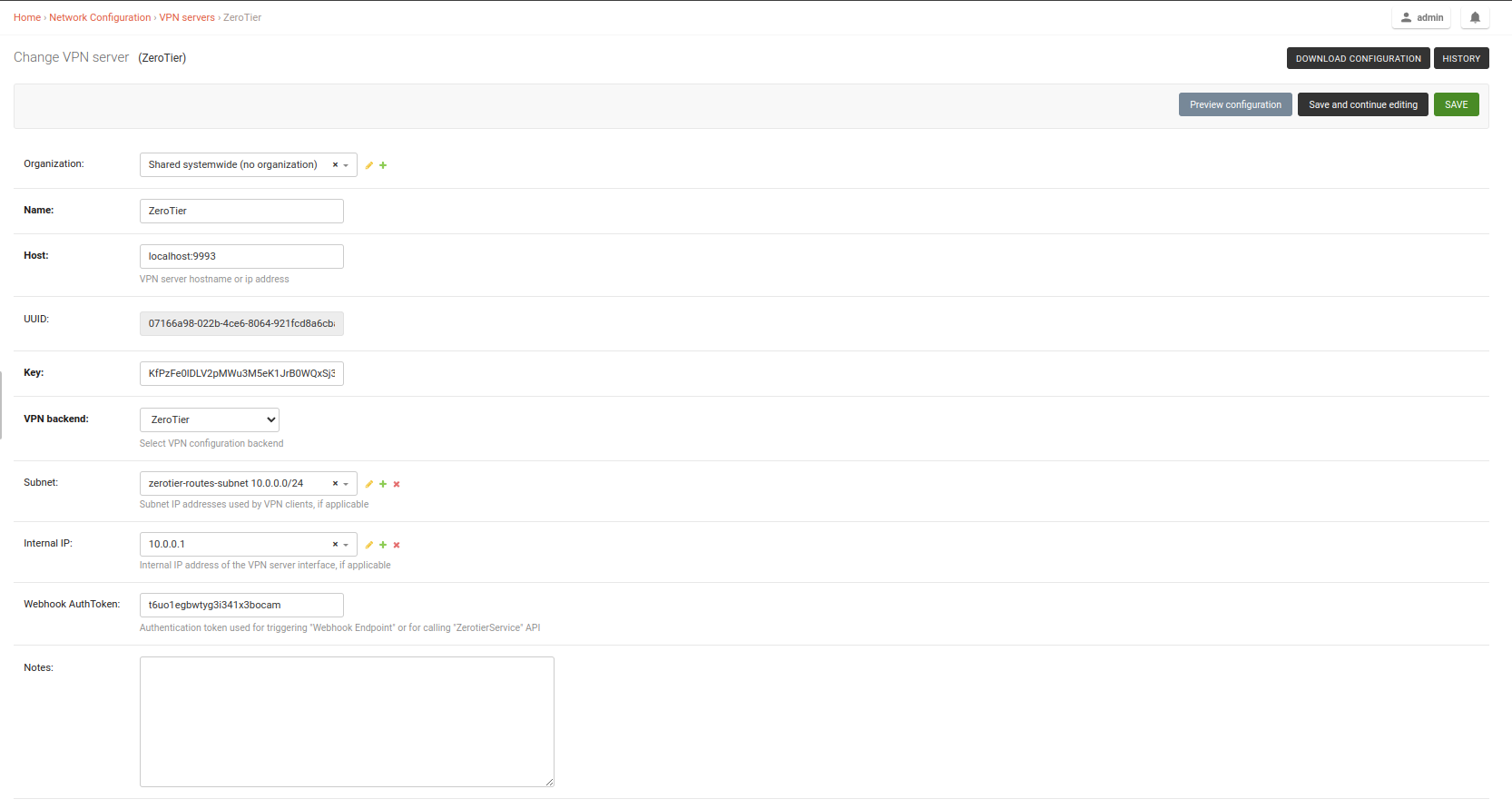
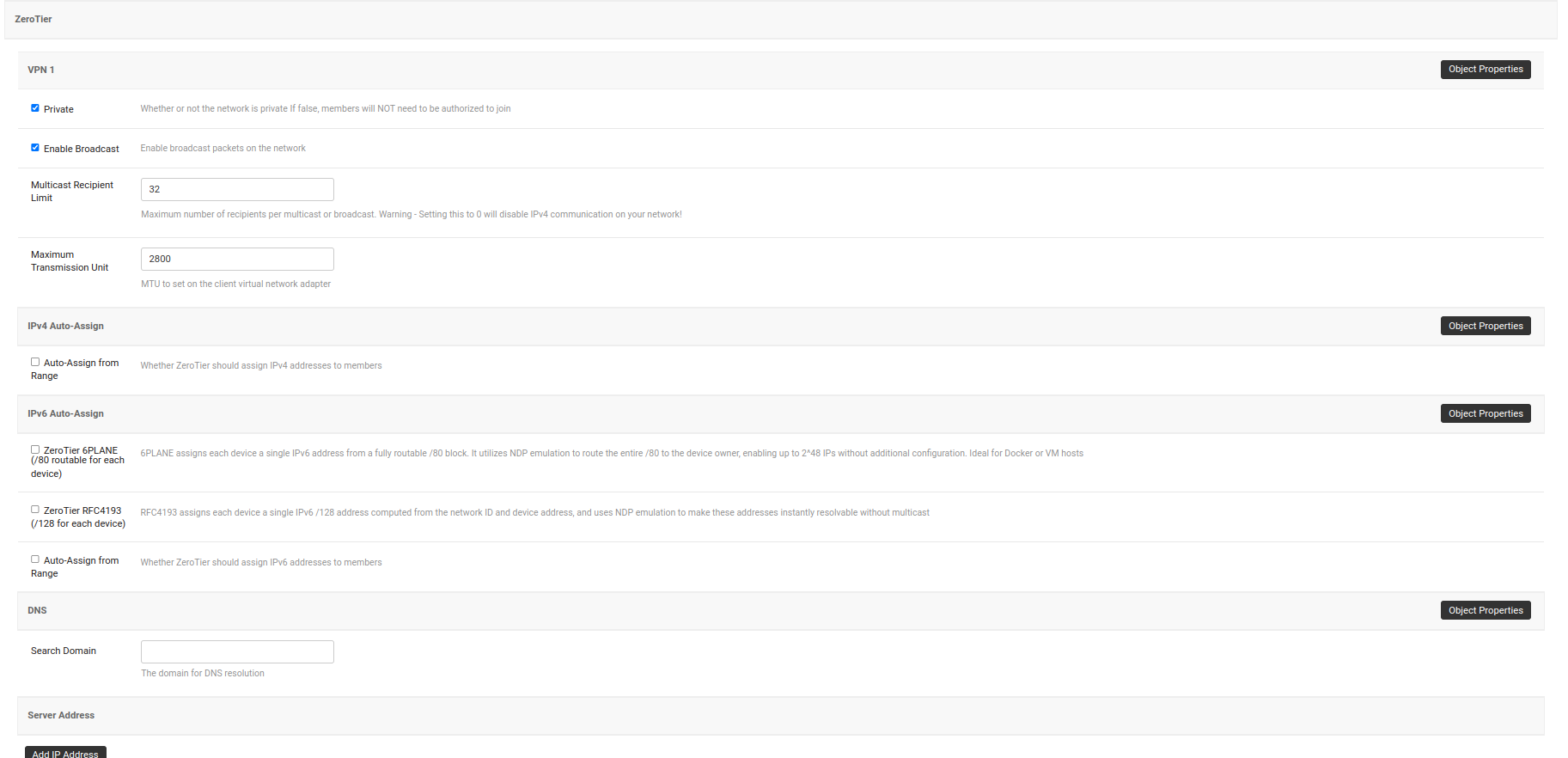
After clicking on Save and continue editing, OpenWISP automatically detects the node address of the ZeroTier controller and creates a ZeroTier network. The network_id of this network can be viewed in the System Defined Variables section, where it also provides internal IP address information.
3. Create VPN Client Template for ZeroTier VPN Server
Visit
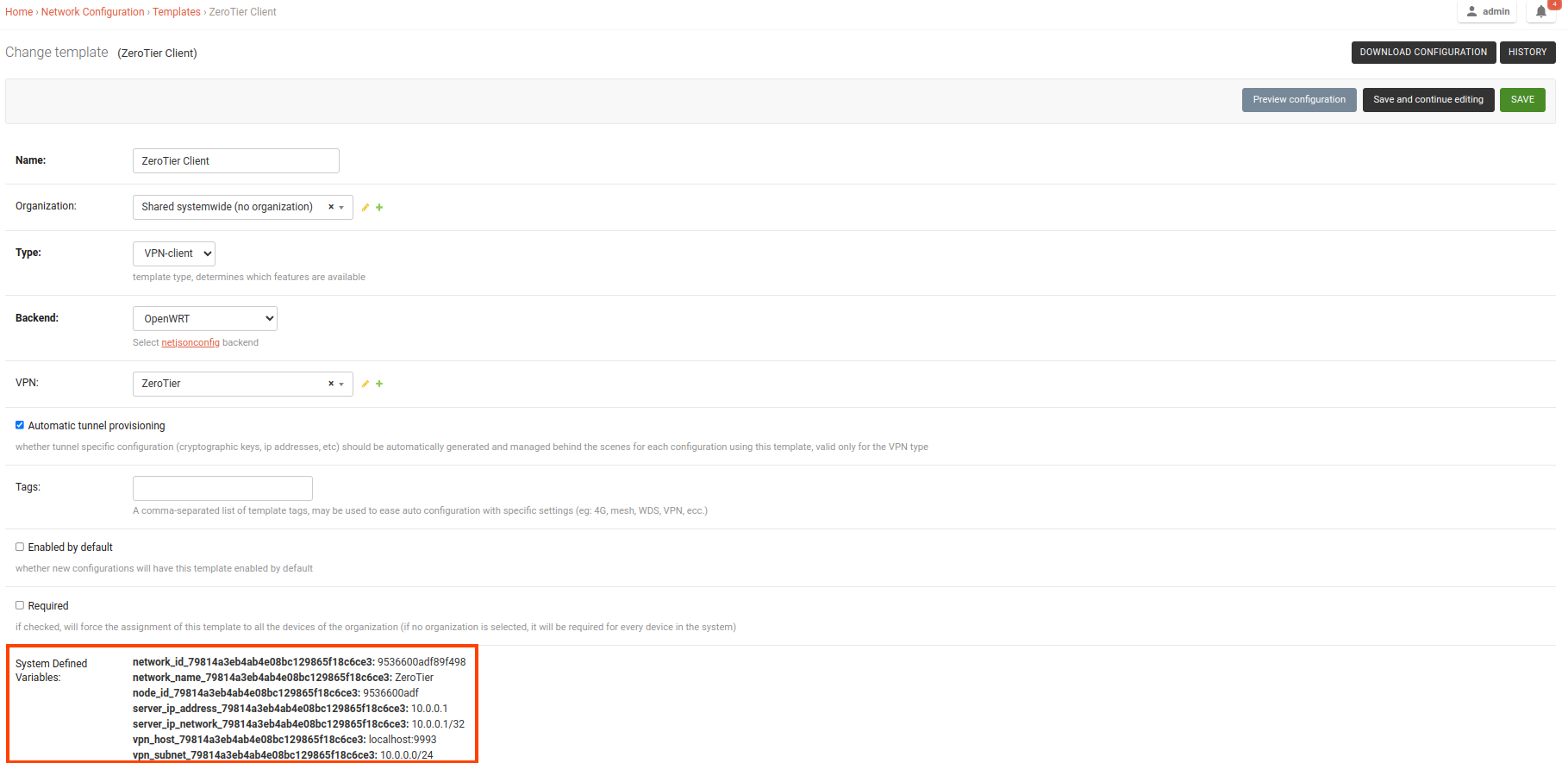
/admin/config/template/add/to add a new template.Set
ZeroTier Clientas Name (you can set whatever you want) and selectVPN-clientas type from the dropdown list.The Backend field refers to the backend of the device this template can be applied to. For this example, we will leave it to
OpenWrt.Select the correct VPN server from the dropdown for the VPN field. Here it is
ZeroTier.Ensure that the Automatic tunnel provisioning option is checked. This will enable OpenWISP to automatically provision an IP address and ZeroTier identity secrets (used for assigning member IDs) for each ZeroTier VPN client.
After clicking on Save and continue editing button, you will see details of ZeroTier VPN server in System Defined Variables. The template configuration will be automatically generated which you can tweak accordingly. We will use the automatically generated VPN client configuration for this example.
Note
OpenWISP uses zerotier-idtool to manage ZeroTier identity secrets. Please make sure that you have ZeroTier package installed on the server.
4. Apply ZeroTier VPN Template to Devices
Note
This step assumes that you already have a device registered on OpenWISP. Register or create a device before proceeding.
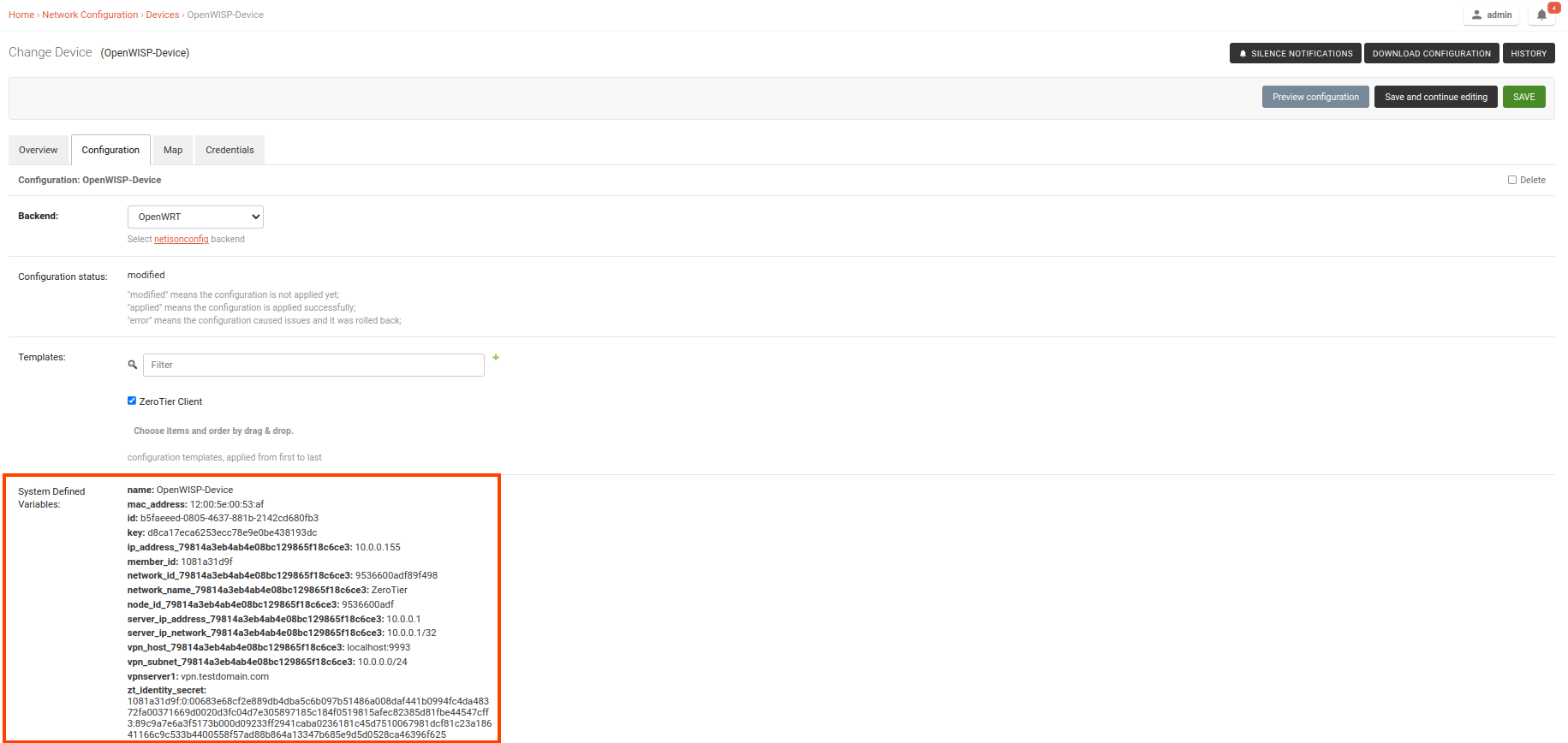
Open the Configuration tab of the concerned device.
Select the ZeroTier Client template.
Upon clicking the Save and Continue Editing button, you will see entries in the System Defined Variables section. These entries will include zerotier_member_id, identity_secret, and the internal IP address of the ZeroTier client (network member) on the device, along with details of the VPN server.
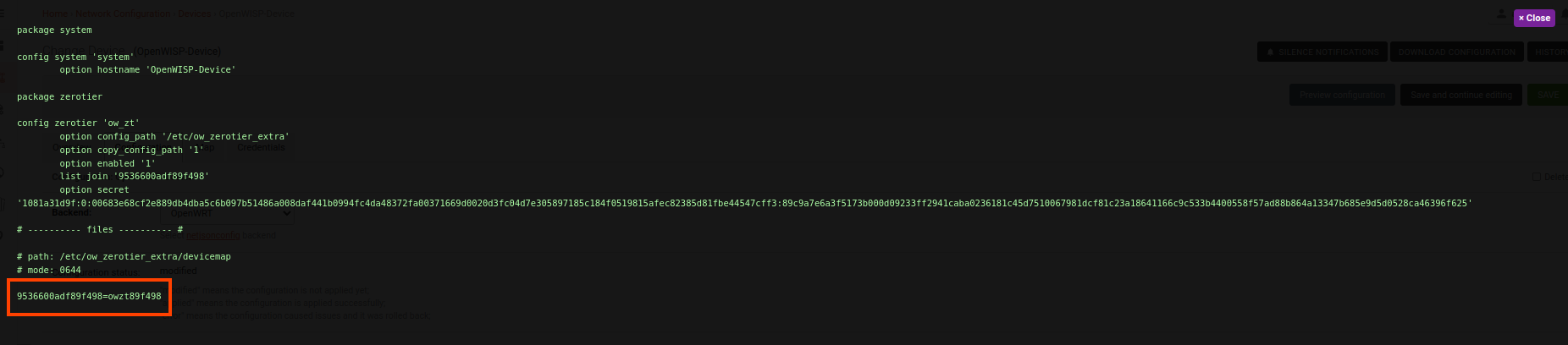
Once the configuration is successfully applied to the device, you will notice a new ZeroTier interface that is up and running. This interface will have the name
owzt89f498(whereowztis followed by the last six hexadecimal characters of the ZeroTier network ID).
Congratulations! You've successfully configured OpenWISP to manage ZeroTier tunnels on your devices.
See also
You may also want to explore other automated VPN tunnel provisioning options: